Contents of this article
In this article I describe Port Security of layer 2 switching in networking for CCNA exam. It is necessary to know about some network security basic concepts along with management of networking devices. We know there are a lots of threats available on internet. Similarly for any network there are many ways to effect the network from virus and hackers. If your network is connected with internet, it is not safe.
There are many types of vulnerability in a network connected with internet. Hackers from all over the world always try to get information from any network. You can safe your network from these attacks by understanding some network security basic concepts. Now a lots of devices transfers data over the internet over wired, wireless and cellular networks.
In this article the main focus is on the Port Security of layer 2 switching by port binding. I also give some idea about the some other related terms to Port Security of layer 2 switching.
What is network security ?
Before describe the Port Security of layer 2 switching in networking first thing to know is network security. The Network security is necessary to protect the own networking devices and clients from unauthorized access, destruction and malfunction etc. Internet is the main resource of security threats. We manage the network for protection from these threats. We can say network security is all about to protect our internet connected computers from virus and hackers. You can manage our network security by using some firewalls, router etc. We allow unauthorized access to unknown persons by compromising own network security.
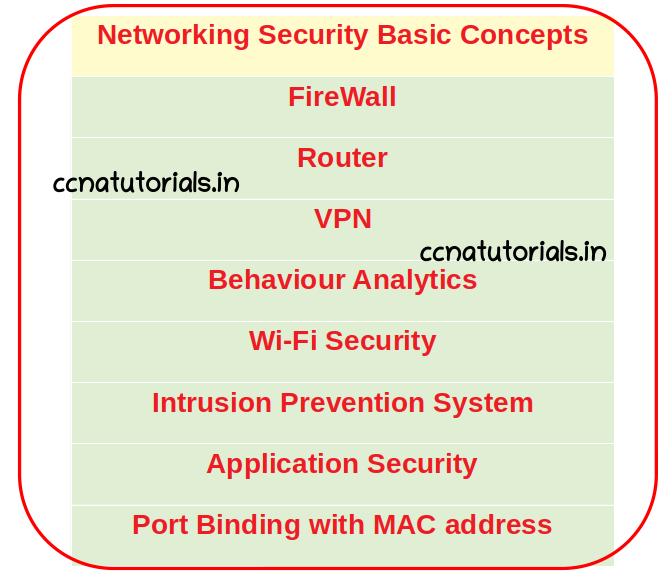
Network security methods
Port Security of layer 2 switching can help to keep secure the network from local threats. There are many devices available to keep secure your network from cyber attack. You required to know the network security basic concepts to use these devices smartly. We can deny the incoming traffic on port basis.
Firewall allow us to block the incoming traffic from unwanted ports. We can allow what kind of service request we want to enter in our own network. Similarly there are many methods and device can be used for various kind of network security. Some common methods used for network security are below.
Access control to our network devices.
Network devices are accessible from inside of network as well as outside of network. Hackers can modify or damage our network device configurations. Configure the access control of networking devices with very precautions. You can change the access port from outside.
It is not necessary the hacker attacks from outside, they can also attack from inside of the network. The main aim of a network administrator should be to keep secure the access panel of networking devices. Always change the default username and password in the networking devices to keep them secure from unauthorized access.Port Security of layer 2 switching can help to keep secure the network from unauthorized access to the devices.
Firewall for network security
Firewall is very common device used by network administrators to keep secure the network. There are two types of firewall available one is hardware device and another is software basis. Software basis firewall can be used for particular computer or server. In case of network security I am talking about the hardware device. The firewall can be configure to enter the traffic for a particular service like https service on port 443.
A firewall deny all incoming traffic by default. Network administrator require to configure the firewall according to requirement of services. Some network provides mail service some web services on internet. Firewalls can be configured accordingly. Firewall also prevent the unwanted traffic from network to out side. Firewall works like a gatekeeper for a network.
Application security in network
Generally network provides the application services like web services, mail services etc. Every application service run on a particular network port. For example web services are accessible on port 80 and 443. Attacker try to enter into the network from these open ports. We require to keep these ports secure. Attackers try to find the vulnerabilities in the application to modify or damage the application. To avoid such type attacks we can use application prevention systems like UTM.
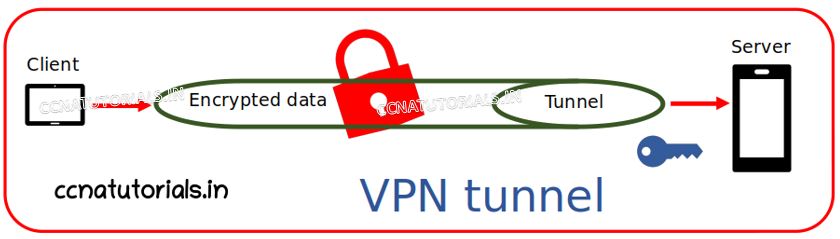
Creation of VPN in routers of the network
VPN stands for Virtual Private Network. VPN configured in the end to end routers over the internet to keep our data safe. A VPN encrypt the connection between networks in a WAN. Data encrypt at the end of transmission and decrypt at the end of reception. Authentication keys are used to encrypt and decrypt the data. These keys are secure. A data flow tunnel created at the two end points of different network.
Analytics of data in a network
Analytics of data means the behaviour of data flow in the network. You can use the analytics of data to keep secure your network. For example if you see the data flow rate of different service then you can imagine the data threat and protect it. Some behavioral analytics tools provides features to detect automatically activities and protect the data.
Wi-Fi security in the network
Wi-Fi is very common method of communication in today life. You can secure the Wi-Fi network by using different encryption methods. Never keep your Wi-Fi in open mode. Open means no need of password to connect the Wi-Fi network.
IPS Intrusion Prevention System in network.
IPS are hardware like firewall and router. The IPS provide additional layer of security to the network. The IPS automatically detects the unwanted traffic access from the network and drop it. IPS works by using the database in it. The data base of IPS contains the common threat data and deny the access of network.
Port Security of layer 2 switching in brief
Port Security of layer 2 switching is most important thing to use in a network for security. Switchports allow any endpoint device to connect with the network. It is entire upon the network administrator whether to allow a new device or not. If the switchports remain open for all with no security, any device can connect with the network. But if you predefined some rules by port binding then only permitted devices can connect with the network. This feature is well known as Port Security of layer 2 switching.
Always keep your network switch switchports in secure mode by using the Port Security of layer 2 switching. MAC binding is very strong method to keep secure the network from unauthorized access. Port Security of layer 2 switching allow to shut down the ports which are not in use. networking always keep your network switch switchports in secure mode. MAC binding in Port Security of layer 2 switching is very strong method to keep secure the network from unauthorized access. Shut down the ports on which the policy violation found in the network.
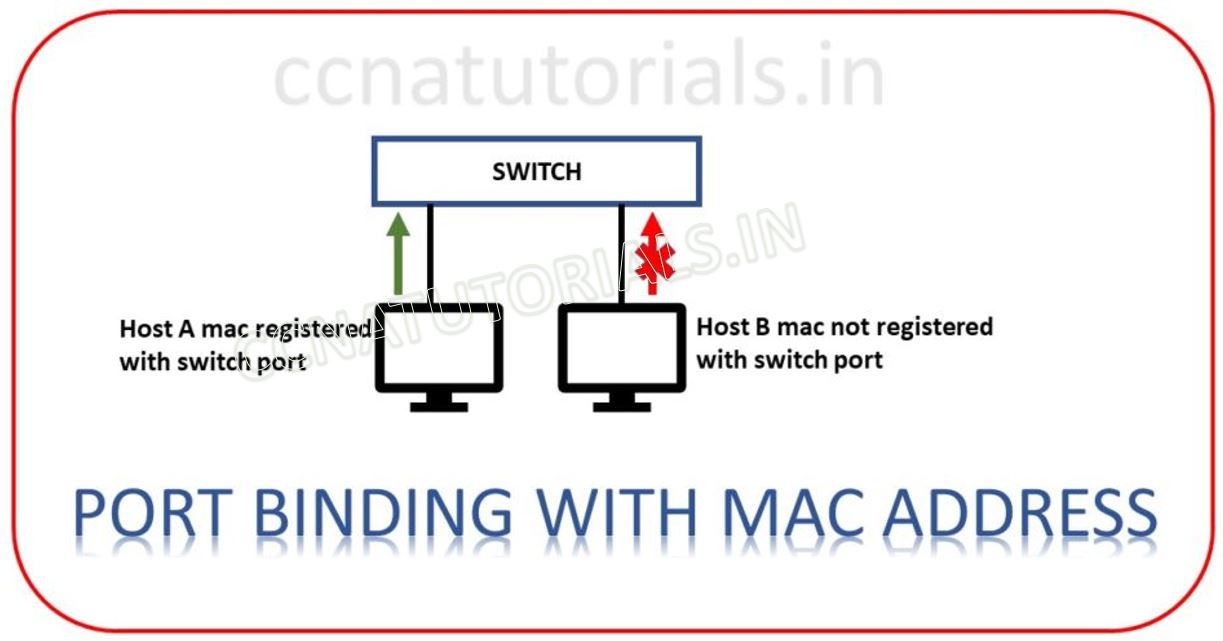
MAC address binding in Port Security of layer 2 switching
A switchport of a switch may be work as weak link at data link layer in networking. Data link layer is layer 2 in the OSI reference model. The modern switch provide some advance features to bind the switchport with a perticular MAC address. This feature avoid the connectivity to unauthorized devices in the network. This feature allow to identify the authorized devices for the network. The port will not receive or forward the data packets from unauthorized MAC address device.
The main function of Port Security of layer 2 switching is to identify the frame address and filter the packets. When a secure port receives a frame, the source and destination MAC address of the frame compared with the MAC address table. If any suspected or new MAC address found as a source of the frame, the packet immediately dropped. This function provide an additional layer of security to the network. By default the switchport shutdown on getting such activities.
Configuration of Port Security of layer 2 switching
Some commands can be used for Port Security of layer 2 switching. We understand that without binding ports of a switch any device can join to the network via the switchport. This is not a good thing and a security breach of the network. Port security of layer 2 switching is necessary to avoid such things. We know each device have its own unique hardware address called MAC address. This MAC address is used to bind a port with a particular device.
Remember Wi-Fi, How we connect a device to wireless network. There are many security method to keep secure the wireless network. There are some security feature available in layer 2 switches. One of these feature is port binding with MAC address. Without port security anyone can add a device in network. Also there are chances of adding hub or switch with a unsecured port.
Forward and filter MAC database can be used for port security of layer 2 switching. You can fix a particular MAC with a interface. Except this MAC address hardware no any other device can access the network the same port. You can limit the number of MAC addresses that can be assigned dynamically to a port, set static MAC addresses.
You can also set penalties for unauthorized devices. You can shut down the port on policy violation. Shutting down on policy violation is the best option to keep secure the network. By default all ports are enabled. You have to shut down the unused ports firstly. Port binding is a big exercise. You have to find MAC address of each device in your network. This one time exercise is very necessary to keep secure your network.
Options for configuring port security of layer 2 switching
Cisco switch port remains in desire mode by default which allow to add any device in the network. Desire mode means, if any switch connected to port then mode of port automatically changed to trunk mode. Firstly we have to convert the desire mode to access mode for all ports. Below is port security configuration for switch name switch-demo.
Switch-Demo#config t Switch-Demo(config)#int f1/1 Switch-Demo(config-if)#switchport mode access Switch-Demo(config-if)#switchport port-security Switch-Demo(config-if)#switchport port-security ? ageing Port-security ageing commands mac-address Secure mac address maximum Max secure addresses violation Security violation mode
You can see in above command lines that switchport port-security command have four options. You can use the switchport port-security mac-address command to assign particular MAC addresses to a switch port.
switchport port-security command can be used to define the poliy on violation. Following action can be taken on security violation.
Protect mode in Port Security of layer 2 switching
Protect option drop the frames with unknown source MAC address. Switch will check the MAC address header and if found it unknown. All the frames will droped which are coming from unknown source.
Restrict mode in Port Security of layer 2 switching
Restrict option also drops the frames of unknown source address. The additional feature in this mode is that, it generates log messages for such events. You can see these logs and find the violance policy device.
Shutdown mode in Port Security of layer 2 switching
By default shutdown mode set for port security violation. This mode will shut down the port and no communication provides by these ports. Once shutdown you have to keep no shut the ports manually. This mode also generates log for the event and you can see these logs manually.
To fix the maximum numbers of device can connects on an interface following command used.
Switch-Demo#config t Switch-Demo(config)#int f1/1 Switch-Demo(config-if)#switchport port-security maximum 1 Switch-Demo(config-if)#switchport port-security violation shutdown
Following commands can be used to keep fix the MAC address on a port. By using these command we put the MAC address manually in the MAC table. So we can use the Port Security of layer 2 switching for MAC binding.
Switch-Demo#config t Switch-Demo(config)#int f1/1 Switch-Demo(config-if)#switchport port-security Switch-Demo(config-if)#switchport port-security violation restrict Switch-Demo(config-if)#switchport port-security mac-address aa.bb.cc.dd.ee.ff
You can see the Port Security of layer 2 switching configuration by using following command in the CLI of the switch.
Switch-Demo#config t Switch-Demo(config)#int f1/1 Switch-Demo(config-if)#do show port-security
In this article I describe some terms related to Port Security of layer 2 switching as well as I give an example to configure the Port Security in a Cisco switch. I hope you found this article helpful. For any query or suggestion on this topic you may drop a comment below or contact us. We always welcome your suggestion for this website.



