Contents of this article
In this article, I describe The Privileged Exec Mode on a Router. Routers are critical components of computer networks, responsible for directing data traffic between different network segments. In a network administrator’s toolkit, the router’s command-line interface (CLI) is a powerful tool for configuring, managing, and troubleshooting routers. One key aspect of router CLI is the Privileged Exec Mode on a Router, often referred to as “enable mode” or simply “privileged mode.” In this comprehensive exploration, we will delve into the purpose and significance of The Privileged Exec Mode on a Router.
Understanding Router CLI Modes
Before we dive into the specifics of The Privileged Exec Mode on a Router, it’s important to understand that router CLI operates in different modes. Each mode serves a distinct purpose, and users have varying levels of access and control in each mode. The primary CLI modes on a Cisco router are:
- User Exec Mode (
>): When you first connect to a router’s CLI, you enter user exec mode. It is indicated by the>prompt. In this mode, users have limited access and can execute basic commands likeping,show, andenable. - Privileged Exec Mode (
#) – Enable Mode: Privileged exec mode, often referred to as enable mode, is the next level of access in the CLI. It is indicated by the#prompt. In this mode, users have elevated privileges and can execute a broader range of commands, including those that can modify router configurations. - Global Configuration Mode (
(config)#): This mode allows users to make changes to the router’s global configuration settings. It is indicated by the(config)#prompt. In this mode, users can configure various parameters, such as setting IP addresses, defining access control lists (ACLs), and configuring routing protocols. - Interface Configuration Mode (
(config-if)#): Users enter this mode to configure specific router interfaces (e.g., Ethernet, serial). It is indicated by the(config-if)#prompt. In this mode, users can configure settings like IP addresses, encapsulation, and interface-specific parameters. - Subinterface Configuration Mode (
(config-subif)#) – Optional: In some cases, when dealing with subinterfaces (e.g., for VLANs or virtual routing and forwarding – VRF), users can access a subinterface configuration mode. It is indicated by the(config-subif)#prompt.
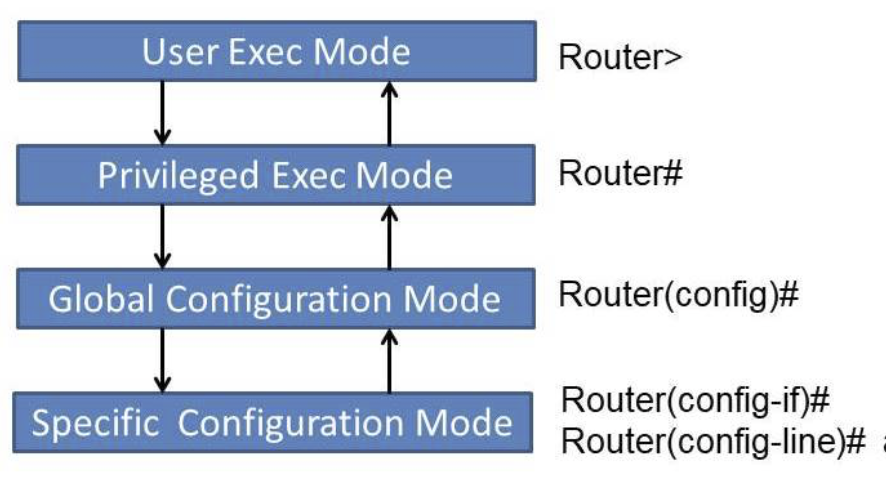
Now, let’s focus on the “privileged exec” mode, its purpose, and why it is a crucial component of router administration.
Purpose of the Privileged Exec Mode on a Router
The Privileged Exec Mode on a Router, commonly referred to as enable mode, is a pivotal component of router CLI for several reasons:
1. Enhanced Privileges:
In enable mode, users gain elevated privileges compared to user exec mode. These elevated privileges are essential for executing commands that can modify the router’s configuration, access sensitive information, and perform advanced network diagnostics. For example, users in enable mode can configure routing protocols, modify access control lists (ACLs), and view system logs.
2. Configuration Access:
One of the primary purposes of enable mode is to grant access to the router’s configuration. Users can enter global configuration mode from enable mode, enabling them to make changes to the router’s settings. Configuration tasks include setting IP addresses, configuring routing protocols, and defining security policies.
3. Network Troubleshooting:
Enable mode is indispensable for network troubleshooting and diagnostics. Users can execute diagnostic commands like show, ping, traceroute, and debug to investigate network issues, examine routing tables, check interface status, and analyze traffic patterns. These tools are essential for identifying and resolving network problems effectively.
4. Security:
Router security is a paramount concern in network administration. Enable mode acts as a security barrier by requiring authentication to access privileged commands. Users must enter a password or use other authentication methods, such as Secure Shell (SSH) or Telnet, to enter enable mode. This helps prevent unauthorized access and configuration changes, safeguarding the integrity of the network.
5. Administrative Control:
Enable mode is also the gateway to administrative tasks, such as saving router configurations, reloading the router, and controlling system processes. Users can save their configuration changes to non-volatile memory, ensuring that the configuration persists after a router reboot. Additionally, administrative tasks in enable mode allow for efficient router maintenance.
Accessing The Privileged Exec Mode on a Router
Accessing “privileged exec” mode requires authentication and involves a few steps. Here’s how to enter enable mode:
- Connect to the Router: Establish a connection to the router’s CLI using a terminal emulator program (e.g., PuTTY) or a console cable. You typically start in user exec mode.
- Access User Exec Mode: After connecting, you’ll see a prompt ending with
>, indicating user exec mode. In this mode, you can execute basic commands but cannot make configuration changes. - Enter Enable Mode: To enter enable mode, use the
enablecommand:
Router> enableYou will be prompted to enter the enable password or another form of authentication, depending on your router’s security configuration.
- Enter Enable Password: After you’ve entered the
enablecommand, you’ll be prompted to provide the enable password. Once authenticated, you will be granted access to enable mode with the#prompt.
Router# You now have elevated privileges and can execute a broader range of commands.
#
Best Practices for Using “Privileged Exec” Mode
Using enable mode effectively and securely is crucial for router administration. Here are some best practices:
- Strong Passwords: Ensure that you set strong, unique passwords for enable mode access. Use a combination of upper and lower-case letters, numbers, and special characters. Regularly update passwords for security.
- Secure Remote Access: If you allow remote access to the router, use secure protocols like SSH and implement access control lists (ACLs) to restrict who can connect remotely.
- Logout After Use: Always exit enable mode and log out when your administrative tasks are complete. Leaving an active session open poses a security risk.
- Limit Access: Implement role-based access control (RBAC) to restrict access to specific commands and configurations based on user roles and responsibilities.
- Use Command Logging: Enable command logging to record all commands executed in enable mode. This provides an audit trail for troubleshooting and security analysis.
- Regular Backups: Create regular backups of your router configurations in case of emergencies or configuration errors.
- Stay Informed: Stay up-to-date with router security advisories and patches. Ensure your router’s operating system is regularly updated to address vulnerabilities.
Conclusion on The Privileged Exec Mode on a Router
The Privileged Exec Mode on a Router, often simply referred to as enable mode, is a critical component of router administration. It grants users elevated privileges, allowing them to configure, manage, and troubleshoot routers effectively. Enable mode is the gateway to the router’s configuration, diagnostic tools, and administrative tasks. It also plays a crucial role in network security by requiring authentication to access privileged commands. Following best practices for using enable mode ensures that router administration is both efficient and secure, ultimately contributing to the stability and reliability of the network. Understanding the significance of enable mode is essential for network administrators and engineers working with routers in diverse networking environments.






