In this article I describe the methods to for mitigating threats at the access layer in switch. It is necessary to know about some network security basic concepts along with management of networking devices. We know there are a lots of threats available on internet. Similarly for any network there are many ways to effect the network from virus and hackers. If your network is connected with internet, it is not safe.
There are many types of vulnerability in a network connected with internet. Hackers from all over the world always try to get information from any network. You can safe your network from these attacks by understanding some network security basic concepts. Now a lots of devices transfers data over the internet over wired, wireless and cellular networks.
Network security protects the devices from unauthorized access and malfunction activities. Malfunction activities can modify or destroy the data. The major cause of data theft is frequently use of internet from mobile and computers. We share personal data on social sites and do financial transaction on internet. The data shared on internet is always on risk from hackers and attackers. To keep safe the data from unauthorized access network security is necessary. We can prevent the attacks on our devices by aware about network security basic concepts.
Network security is necessary to protect the own networking devices and clients from unauthorized access, destruction and malfunction etc. Internet is the main resource of security threats. We manage the network for protection from these threats. We can say network security is all about to protect our internet connected computers from virus and hackers. You can manage our network security by using some firewalls, router etc. We allow unauthorized access to unknown persons by compromising own network security.
There are many types of threats for network devices. A network Administrator should be aware about common threats at access layer of switch. The most common threats at access layer is to gain the sensitive information of a user like username passwords etc. The open network is full of risk of threats because any one can access the network to any switch port. So we use multiple types of network security to reduce threats at access layer in switch. Let’s discuss about some common methods for mitigating threats at the access layer in switch.
MAC Address Flooding Threats at the access layer in switch
We know the layer 2 switch maintain a table for MAC addresses of connected devices. It is very necessary to mitigating threats at the access layer. MAC address flood threat can delete or manipulate the data of MAC table. It is generally known as Denial of Service (DoS) attacks. The switch have a fix memory space to keep the data of MAC address. The switch do frame forwarding, filtering at layer 2 access layer. MAC address flooding attack overflow the MAC address learning capacity and frame forwarding will disturb. Port Security feature can be used to reduce the mac address flooding threat. Administrator can assign the unique MAC address with specific ports. The mac address learning property will stop hence the MAC address table used properly. If a different MAC address request come to save in MAC table, the port security deny it. You can also set the result of violation of policy like shutdown port.
Spanning Tree Protocol (STP) threats at the access layer in switch
Spanning Tree Protocol prevent the network from potential loops. Spanning tree protocol is very useful protocol for mitigating threats at the access layer in switch. Without STP the LAN may be stop functioning. The spanning tree protocol works on LAN switched networks. Configuration of STP keep LAN stable. An attacker can insert new STP device in network to alter the configuration of existing STP. This activity can affect the traffic flow in network. The security of the traffic can be compromised without configuration of STP.
Address Resolution Protocol (ARP) spoofing Attacks
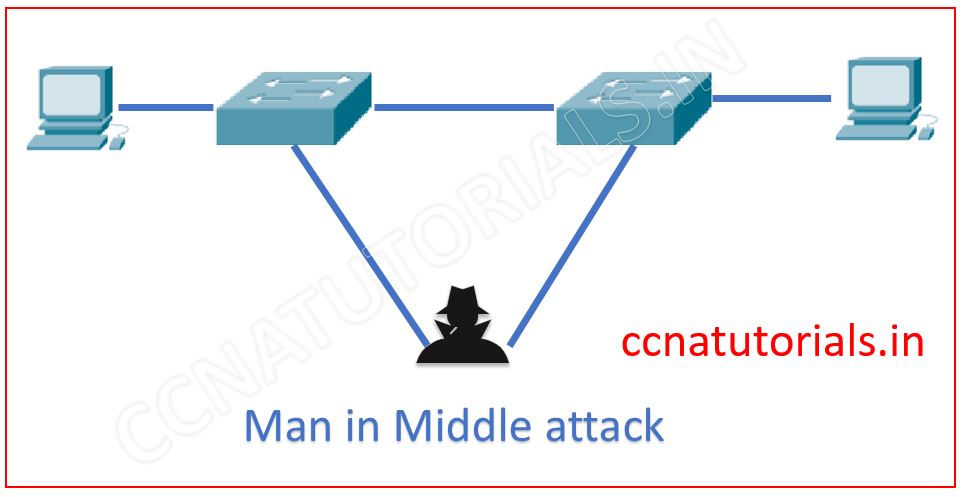
Address resolution protocol spoofing attacks are very common threat in any switched network. ARP is used in all networks to map the MAC address and IP address of network devices and nodes. The attacker request to register a MAC address with wrong IP address. If wrong IP address mapped with MAC address the data traffic can be compromised. This is generally known as man in middle attack.
Media Access Control (MAC) spoofing attack
The purpose of MAC spoofing attack is to manipulate the MAC address database in the switch. You can understand if the MAC address is changed of any device then the traffic will received by the wrong device. An attacker can get the useful information from any device. Mac spoofing attack can perform a denial of service attack on any device.
VLAN Hopping attack
We know all switch contain VLAN and each port of switch belongs to any VLAN. By default all switchports belongs to a single VLAN. User can create more VLANs and separate the switchports for different VLAN. VLAN hopping attack can manipulate the VLAN database of the switch. The aim of VLAN hopping attack is to divert the traffic from original VLAN to a wrong VLAN.
Dynamic Host Configuration Protocol (DHCP) Spoofing attack
DHCP spoofing attack also done to manipulate the IP address system of a Local Network. The function of DHCP protocol is to allot the IP address to any newly connected device. Network administrator configure the DHCP according to the IP schema. In DHCP spoofing attack a wrong DHCP server placed in the network with different IP schema. When a new device connected in the network it is possible the device can get wrong IP address. This type of attack can divert traffic from any host to a wrong gateway. Thus the attacker can steal the important information from any client in the network.
Summary for mitigating threats at the access layer in switch
I provide you some common threats at the access layer in switch. Some of them can be reduce by default by the switch. Network administrator is responsible to check and identify these threats time to time. Open network is very easy target for attackers to steal the information from any host.
I hope you found this article helpful. For any query or suggestion on this article you may drop a comment below or contact us. your suggestions are always welcome by us.



