In this article I describe the IPsec Internet Protocol Security in computer network for CCNA exam. IPsec Internet Protocol Security is related to internet layer of TCP/IP Suite model. The IPsec Internet Protocol Security provides the security, encryption, decryption, VPN etc between two different networks on internet. IPsec Internet Protocol Security provide the platform for data security at the internet layer of TCP/IP network. The IPsec Internet Protocol Security use multiple authentication and encryption of data at internet layer to provide the security to the data packets in the network. IPsec Internet Protocol Security also used some algorithms for cryptographic for encryption and decryption of data.
Routing and Routed Protocols provides the connectivity between different networks for data packets flow from one network to another network. A standard routing table is maintained by the routers for data packet flow between different networks.
Before going to learn about IPsec Internet Protocol Security in detail, we need to remember the OSI suite and TCP/IP suite model. There are many manufacturer of computer machine in the market. Initially when computers became single user public computer. The computers communicate with only same brand machines. It happens because there was no any fix standard for data transfer between different devices. It is very difficult to make communication with each other when the hardware are of different brands or company. In this article I describe the some basic part of OSI reference layer and TCP/IP Suite model basic concepts in networking with the IPsec Internet Protocol Security.
OSI reference model basic concepts
OSI reference model in computer network followed by various vendors to overcome the compatibility problem. After implementation of OSI reference model in computer network, equality maintains by all manufacturer. In 1970 the Open Systems Interconnection (OSI) reference model was created by the International Organisation for Standardisation (ISO). The OSI model was meant to create inter-operable network with different manufactured devices. In this article I describe some layered approach of TCP/IP Suite model basic concepts in computer network. Before understanding the TCP/IP Suite model basic concepts it is necessary to know about the 7 layers of OSI reference model because the basic work of each layer is described in the OSI reference model. You can read the full article related to OSI reference model in computer networking here.
Importance of OSI reference model for IPsec Internet Protocol Security
Before going to know about the IPsec Internet Protocol Security. It is necessary to know the function of layers in OSI model and TCP/IP model. Initially not only hardware but software also not supported for work the different computer brand. It became very difficult for all computer users to working without implementation of OSI reference model in computer network. It is necessary then to make some common protocols for all vendors of computer. Before implementation of OSI reference model in computer network, all vendors implements their own protocols on computer hardware and software.
In networking OSI reference model became helpful. OSI reference model describes the flow of data between nodes in any network. Data from one computer application to another computer application transfer by following some common protocols. The OSI reference layer also become beneficial for troubleshooting the network problems. TCP/IP and Cisco three layered hierarchical model of Cisco became more helpful alongside the OSI reference model.
The Layered Approach in computer network
The Layered approach was the best way to make equality for all computer devices. Layers are not physical but following some protocols. Protocols are for connectivity, connections, data transfer and more. All manufacturer begin to follow the layered approach for OSI reference model in computer network. The OSI reference model change in TCP/IP reference model and later on Cisco three layered hierarchical model. OSI layer architecture have 7 layers. TCP/IP reference model convert these 7 layers into only four layers. After that Cisco three layered hierarchical model converts these 7 layers into three layers. Some layers combined to work in a single layer.
OSI is acronym for open system interconnection. The OSI is a logical reference OSI reference model in computer network. OSI model helps for data flow between different devices and operating systems. All manufacturer used their own architecture before invention of OSI reference model. It was very difficult to establish data communication between different devices. To overcome this problem international organization for standardization (ISO) created the open systems interconnection (OSI) reference model. OSI reference model make data flow possible between different operating system, devices and hardware. Later the OSI model adopted by Cisco as Cisco three layered hierarchical model.
Structure of OSI reference model related to IPsec Internet Protocol Security
OSI reference model in computer network consist of 7 layers. These 7 layers further divided into two groups. First 3 layers works for application communication and remaining 4 layers works for data flow. Application, presentation and session layers define the application communication. Transport, network, data link and physical layers define the data flow. Networking protocols works only on last four layers.
TCP/IP Suite model basic concepts for IPsec Internet Protocol Security
TCP/IP is acronym for Transmission Control Protocol/Internet Protocol (TCP/IP suite model). In this section of the article I describe about TCP/IP suite model basic concepts in detail. TCP/IP suite model is a reference model like OSI layers. Instead of 7 layers of OSI reference model. TCP/IP suite model consist only four layer. All seven layers are merged into four layers only. TCP/IP suite model was designed and implemented by Department of Defence (DoD). TCP/IP developed to preserve data integrity. The main purpose to develop the TCP/IP is to provide security in the network. A lots of protocols works on each layer to provide a secure network.
It is necessary to understood the protocols used in TCP/IP Suite model basic concepts. IP addressing play an important role in TCP/IP Suite model basic concepts. By using the IP address and subnet masking broadcast domain breaks. It will improve the performance of the network. Breaking broadcast domain increase the data flow speed. Here IP stands for IPV4 only. We ignore the IPV6 for some time in this article. It will make it easy to understand the TCP/IP Suite model basic concepts.
A snap of TCP/IP Suite model basic concepts
In the decade of 1970’s TCP/IP suite model developed by DoD. In the initial stage TCP/IP suite model divided into two segments TCP and IP. Later its name registered with combined name of TCP and IP like TCP/IP model. ARPA, the Advanced Research Projects Agency of DoD officially authorised to use TCP/IP suite model. TCP/IP model was working well so it was adopted by many organisations. In today scenario it is mostly using reference model for networking. Internet is the best example of using TCP/IP.
Process or Application layer of DoD model in TCP/IP Suite model
This is the first layer of TCP/IP of DoD model. It is combination of top three layers of OSI reference model. The functions of Application layer, presentation layer and session layer in OSI model works in single layer process layer. This layer supports the point to point communication and controls the user interface. The data encryption and decryption also done at this layer. Example of some protocols functions at this layer are TLS Transport Layer Security, FTP, LPD, TFTP, SMTP.
Transport layer of DoD model in TCP/IP Suite model
Transport layer of TCP/IP is same as the Transport layer of OSI reference model. It supports the TCP and UDP protocol. This protocol converts the main data segment into packets and transport to the internet layer. The responsibility of Transport layer is to combine the segments and built the data. The data should be reconstruct in its real form. Transport layer is also responsible for creating end-to-end communication between sender and receiver. This layer ensure the delivery of segment in sequence at the receiving device. This property maintains the data integrity.
Internet layer of DoD model in TCP/IP Suite model
Internet layer of TCP/IP is similar to the network layer of OSI reference model. Routing protocols functions on Internet layer of TCP/IP model. Addressing and filtering of packets is main responsibility of Internet layer of TCP/IP model. This layer provides the transmission of packet in the whole network. Some example of protocols functions on internet layer are ICMP, ARP and IP.
Link layer of DoD model in TCP/IP Suite model
Link layer is the least layer of TCP/IP. Basically link layer is combination of data link and physical layer of OSI reference model. Link layer is also known as Network Access layer. It works on MAC address based data transmission. Link layer handles the frame and bits. It receive the bits and constructs frame from merging bits in a sequence. In case of any bit is missing this layer request to re transmit the bits. Ethernet, FDDI, WAP etc functions on this layer. There is no any preset specification for link layer. Link layer functions on any type of existing media.
IPsec Internet Protocol Security Explained in brief
IPsec Internet Protocol Security uses two mechanism for security of IP packets. These are ESP and AH. ESP stands for Encapsulating Security Payload and AH stands for Authentication Header. ESP defined the method for encryption of data packets while AH digitally signed the data packets. IPsec Internet Protocol Security mostly used at the both ends of VPN tunnel to keep the data secure. IPsec Internet Protocol Security also provide the authentication without encryption for data packets in a VPN. IPsec Internet Protocol Security works with both IP protocols IPv4 and IPv6.
IPsec Internet Protocol Security is an internet layer protocol in TCP model. IPsec Internet Protocol Security creates the framework for security on internet protocol. Data security at internet layer is main task of IPsec protocol. Various authentication and encryption methods work to provide the security at internet layer. The packets encrypt and decrypt by predefined rules. These rules followed by IPsec protocol to provide the security at internet layer.
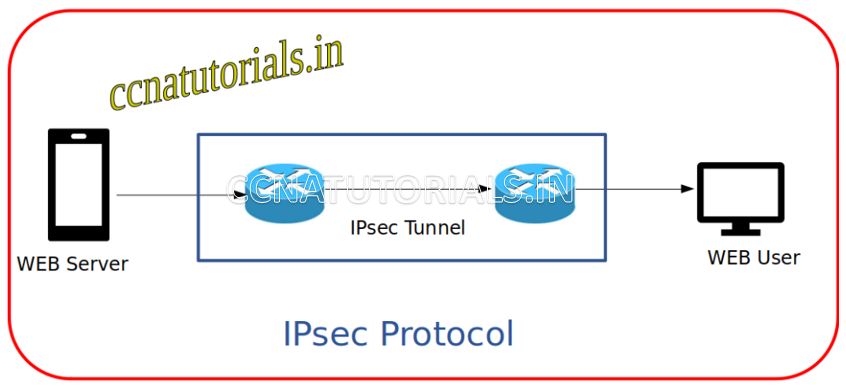
Ipsec protects the data flowing in the network. The data sent from a host to another host via Ipsec tunnelling. The data encrypted before sending on internet at the host end. The encryption done by the router which configured Ipsec. The network via which the data transferred via Ipsec tunnelling is known as VPN. VPN stands for Virtual Private Network. The encryption and decryption data process done at internet layer by router. Later we discuss in brief about the VPN Virtual Private Network.
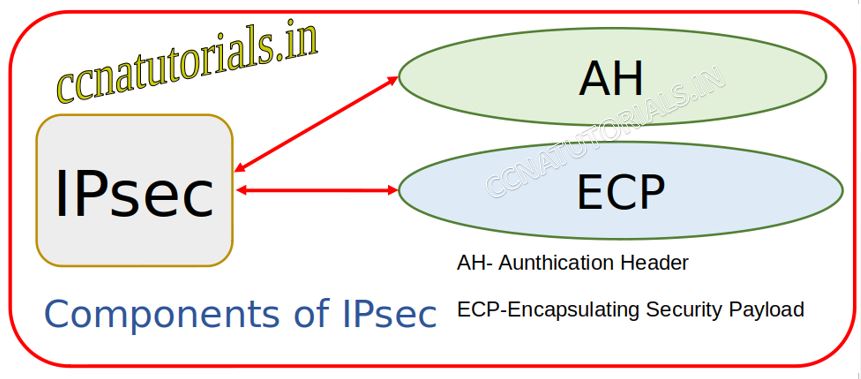
Parts of Ipsec Internet Protocol Security
Ipsec works on authentication and cryptography of data on internet. ESP and AH protocols are two major parts of Ipsec Internet Protocol Security. ESP stands for Encapsulating Security Payload protocol. AH stands for Authentication Header protocol. ESP defines the technique of encrypting data for packets. ESP protocol uses unique keys for encryption and decryption IP packets. AH protocol defines the technique to authentication method for IP Packets.
IPsec protocol supports both Internet protocols IPv4 and IPv6. Some other protocols also used for security without IPsec like HTTPS and TLS. These protocols works differently from IPsec. A terms IKE Internet Key Exchange used for IPsec protocol. IKE protocol allow the hosts to choose the services for packet transfers. These services cryptographic algorithms used for IPsec protocol.
Function of Ipsec Internet Protocol Security
A host required to send the data on internet to another host. The sender host define the method of security for the data. Data can encrypted at earlier application layer or can by use IPsec protocol. It is totally depends on the sender host whether IPsec required or not. IP packets use various techniques for authentication and encryption on internet. The sender and receiving host used IPsec authenticate each other for secure communication. A secure channel created by hosts to send and receive the data in encrypted format.
After creation of secure channel between two hosts over internet. Various algorithm used for authentication and encryption the data. Data flow starts from one host to another host on secure tunnel. After transferring the complete data session ended by the hosts. The IPsec Tunnel terminate by both hosts. It can be done on time out of session.
Some Important Protocols used for IPsec Internet Protocol Security
ESP Encapsulating Security Payload protocol specified in RFC 4303. ESP encrypt the payload of a packet and decrypt the same at the receiver end. AH authentication Header specified in RFC 4302. AH defines additional optional packet header for the data packets. IKE Internet Key Exchange specified in RFC 7296. IKE and IKEv2 allow the hosts to select the services for cryptographic algorithms for encryption. ISAKMP Internet Security Association and Key Management Protocol, defines the services via which the IPSec make secure connection between different networks on the internet. The SAs Security Associations define the direct connection between different hosts which are using the IPsec protocol. A single SA define the connection in a single direction only, so for using a full communication between two hosts in a network we need minimum two SAs.
Working of IPsec Internet Protocol Security
Firstly a host identify that a packet need to be transmitting with IPsec protocol. The host can identify by checking the header of the packet which includes the IP address of source and destination. On getting the information that the packet needs to be transmitted with IPsec Internet Protocol Security, IKE provides the secure channel between the source and destination host for data transfer. IKE works on two modes main mode and aggressive mode. In main mode the security is greater because of setup of tunnel. In main mode the session algorithms and keys exchanged between two hosts from a secure tunnel. In aggressive mode some data passed as plain text and enables hosts to establish secure connection via using the IPsec Internet Protocol Security.
Now after establish a secure tunnel between the two hosts in a network. The IPsec Internet Protocol Security setup IKE phase 2 over the secure channel which is previously set up. Now the hosts share the cryptographic algorithms and transfer the data with each other on this secure tunnel. The data packets encrypted and decrypted by the SAs protocol during transmission. After completion of data transfer the IPsec Internet Protocol Security terminate the session between two hosts in the network.
Ipsec Internet Protocol Security summary
Ipsec supports both internet protocl IPv4 and Ipv6 on internet. Ipsec mostly used for Intranet networks on internet. Between various locations to keep the data transfers securely VPN tunnel used. These VPN tunnel created by Ipsec Protocol. In VPN tunnels each packet goes through authentication, encryption and decryption. Ipsec protocol functions on internet layer in TCP/IP model. A unique key phrase used between sender and receiver host.
In this article I describe the IPsec Internet Protocol Security in computer network for CCNA Exam. I hope you found this article helpful for any query or suggestions you may drop a comment below or contact us. Your suggestions are always welcome by us.




