Contents of this article
In this article I explain the Extended access control list in router. In previous article you learn the standard access control lists in router. Extended Access Control List is a type of ACLs. Access Control Lists in router works as filter to allow or deny the routing updates and packets in particular interface of router. Extended Access Control Lists provides an extra layer of security for network. Access Control Lists control the incoming and outgoing traffic of a network.
Access Control Lists in router works as filter to allow or deny the routing updates and packets in particular interface of router. Access Control Lists provides an extra layer of security for network. An Access Control Lists control the incoming and outgoing traffic of a network. Access Control Lists do only two things permit the packets and deny the packets at layer 3 of OSI reference model.
On arrival a packet at the router interface, the router examined packet header and tally the information with the existing Access Control Lists in router. The comparison of both information give decision whether the packet should be drop or allow. This process works on network layer of the OSI or TCP/IP model. Access Control Lists in router can be apply on entrance or exit interface.
Access Control Lists are set of instructions use to filter the traffic passing through a router interface. The traffic may be incoming or outgoing from an interface. Access Control List is the in integrated facility of IOS of a router. On arrival a packet on interface the router firstly check the destination address of the packet. Then, router check the destination address entry in its routing table. If destination address found in routing table router check for Access Control List on that interface. According to the Access Control Lists the packet permitted or dropped on that interface.
Access Control Lists do only two things permit the packets and deny the packets at layer 3. On arrival a packet at the router interface, the router examined packet header and tally the information with the existing Access Control Lists in router. The comparison of both information give decision whether the packet should be dropped or allow. In this article I brief the configuration of extended access control list in a router.
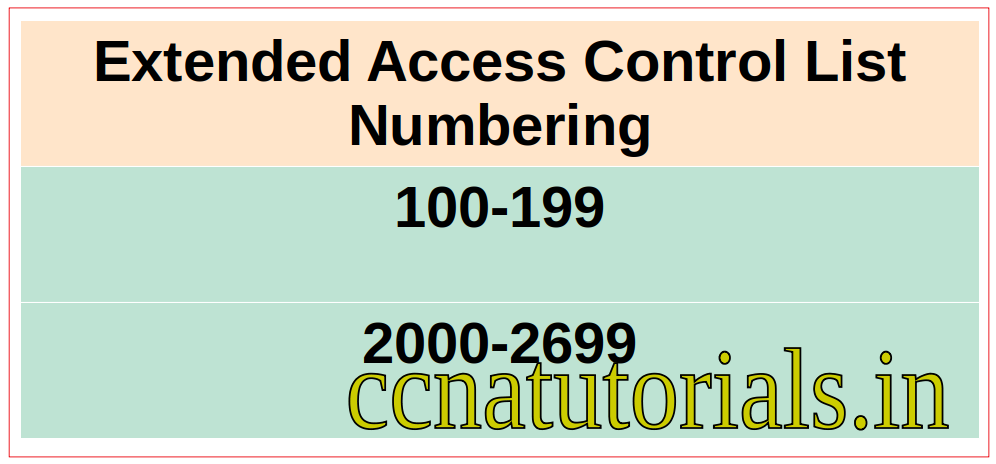
Extended access control list identify by the number of ACLs. The predefined numbers for standard access control list are 100-199 and 2000-2699. Router apply the existing extended access control list on incoming or outgoing packet on a particular interface. Extended access control list works on IP address of source and destination. It can filter the traffic on the basis of protocols like WEB, UDP or email etc. Before going to configure the extended access control list let’s take a look on the features of Extended ACLs in router.
Features of Extended Access Control List
Opposite to the standard access control list the Extended Access Control Lists applied close to the source. Extended ACLs filters the packets on the basis of IP address and protocols. The Extended ACL provide a facility to permitted or deny to a particular service on a particular IP address. Extended ACLs can be created as named ACL and as well as Numbered ACLs. Remember that numbered can not be modified while the named access list can be modified later.
See the commands below in the CLI of router. These commands shows how many services can be managed by the extended ACLs.
Router> Router>en Router#config t Router(config)#access-list 110 ? deny Specify packets to reject permit Specify packets to forward remark Access list entry comment Router(config)#access-list 110 deny ? ahp Authentication Header Protocol eigrp Cisco's EIGRP routing protocol esp Encapsulation Security Payload gre Cisco's GRE tunneling icmp Internet Control Message Protocol ip Any Internet Protocol ospf OSPF routing protocol tcp Transmission Control Protocol udp User Datagram Protocol Router(config)#
Now I am selecting the TCP to block. Following command windows shows the option to deny TCP for a particular IP address. You can see you can permit or deny particular port by using eq tag. So there are many options for using extended access control list.
Router(config)#access-list 110 deny tcp any ? A.B.C.D Destination address any Any destination host eq Match only packets on a given port number gt Match only packets with a greater port number host A single destination host lt Match only packets with a lower port number neq Match only packets not on a given port number range Match only packets in the range of port numbers Router(config)#
You can see what options are available for eq tag by running below command. See the results.
Router(config)#access-list 110 deny tcp any eq ? <0-65535> Port number ftp File Transfer Protocol (21) pop3 Post Office Protocol v3 (110) smtp Simple Mail Transport Protocol (25) telnet Telnet (23) www World Wide Web (HTTP, 80) Router(config)#
I hope you understand how much strong is extended ACLs than standard ACLs. In below example I will show to block only single service FTP from one network to another network.
Configuration of Extended Access Control List in router.
See the network image below. Here we have three different networks connected with a router. Interface GigabitEthernet0/0 connected with network 192.168.1.0/24. Interface GigabitEthernet0/1 connected with network 192.168.2.0/24. Interface GigabitEthernet0/2 connected with network 192.168.3.0/24. A PC in each network connected with the router. IP address of PC1, PC2 and PC3 are 192.168.1.2, 192.168.2.2 and 192.168.3.2 respectively.
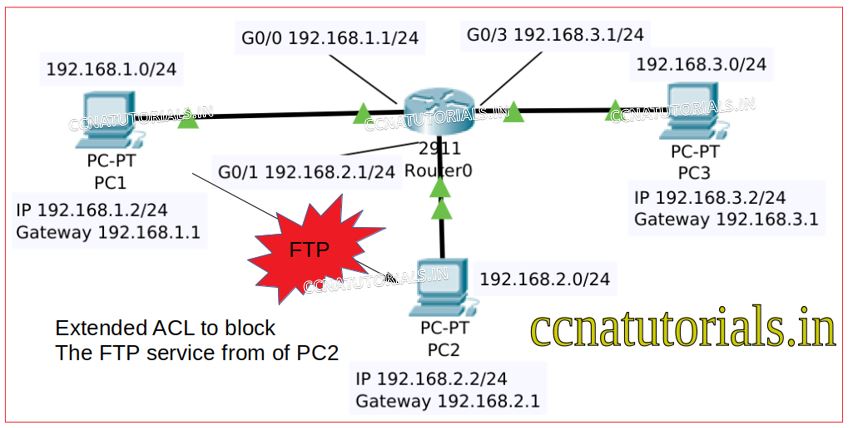
First thing is required is to assign the IP address to all three interfaces of router. These IP address works as gateway for all three networks. To assign the IP addresses on all interfaces run the below commands in CLI of router.
Router>en Router#config t Router(config)#interface gigabitEthernet 0/0 Router(config-if)#ip address 192.168.1.1 255.255.255.0 Router(config-if)#no shut Router(config-if)#exit Router(config)#interface gigabitEthernet 0/1 Router(config-if)#ip address 192.168.2.1 255.255.255.0 Router(config-if)#no shut Router(config-if)#exit Router(config)#interface gigabitEthernet 0/2 Router(config-if)#ip address 192.168.3.1 255.255.255.0 Router(config-if)#no shut Router(config-if)#do wr Building configuration... [OK] Router(config-if)#exit Router(config)#
Now assign the IP address to each PC as shown in figure above. The IP address of connected interfaces will work like gateway for each network. After assigning IP addresses to Pcs ping all Pcs with each other. You found all Pcs are communicating with each other successfully. Here no requirement for IP routing as all networks directly connected with router.
Configure extended ACL in router
My aim is to deny the access of FTP service of PC1 from PC2 and permit all other services. We require to create a Extended access list in router and apply it to appropriate interface. The subnet mask of network 192.168.1.0 is 255.255.255.0 so the wildcard mask will be 0.0.0.255. Configure a Extended access list by running the below commands in CLI.
Router>en Router#config t Router(config)#access-list 110 deny tcp 192.168.1.0 0.0.0.255 eq 21 Router(config)#access-list 110 permit ip any any
A Extended ACL 110 created by running above commands in router. In above command TCP protocol required to filter at the applied interface of router. We also define the port number 21 which is used for FTP protocol in the network. After creation of list the most important part is where to apply this extended ACL. Our requirement here is to block the FTP service for PC2 from PC1 so we applied this extended list on the interface GigabitEthernet0/1. Run the below commands in CLI of router to implement the extended list.
Router>en Router(config)#interface gigabitEthernet 0/1 Router(config-if)#ip access-group 110 out Router(config-if)#exit Router(config)#exit Router#
After running the above command the FTP services will stop for PC2 from PC1. Same configuration can be done by using named extended access control list in router.
Configuration of a named Extended access control list in router
In above exercise I use the Extended access control list by its number 110. you can give it a name at the time of configuration and call it by its name. See the below commands to create named standard ACL similar to above ACL.
Router(config)#ip access-list Extended blockftp Router(config-std-nacl)#deny tcp 192.168.1.0 0.0.0.255 eq 21 Router(config-std-nacl)#permit tcp any any Router(config-std-nacl)#exit
An Extended ACL named blockftp is ready. To apply this ACL on interface GigabitEthernet0/1 run the below commands.
Router(config)#interface gigabitEthernet 0/1 Router(config-if)#ip access-group blockftp out Router(config-if)#exit Router(config)#do wr Building configuration... [OK] Router(config)#
Monitor the access lists
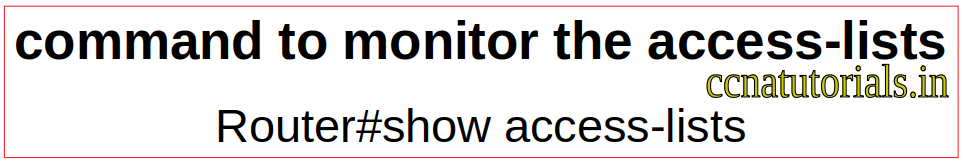
After applying the blockftp ACL on GigabitEthernet0/1 you can see the same result.
I hope you found this article helpful related to Extended access control list and its function in a network. For any query or suggestion on this article you may contact us or drop a comment below. Your suggestions are always welcome by us.







Today, I went to the beachfront with my children. I found a sea shell
and gave it to my 4 year old daughter and said “You can hear the ocean if you put this to your ear.” She put the shell to her
ear and screamed. There was a hermit crab inside and it pinched her
ear. She never wants to go back! LoL I know this is totally off topic but I had to tell someone!
Good replies in return of this question with real arguments and describing everything regarding that.
I have been surfing on-line more than 3 hours as of late, yet I never found any interesting article like yours. It¦s lovely worth enough for me. Personally, if all web owners and bloggers made good content as you did, the internet will be much more useful than ever before.