In this article I describe the method to Configure VLAN in Cisco Switch for CCNA exam. VLAN provides multiple virtual networks in a physical network. We can break a local area network into multiple virtual networks. The devices of same virtual network can communicate with each other without interfere to other virtual network. The switchports of a switch can be used as access port or trunk port. The function of access port and trunk port are different. It may be useful to learn some common terms or VLAN before Configure VLAN in Cisco Switch.
The switch provide a single broadcast domain to all connected devices by default. Each port of switch creates single collision domain. VLAN breaks the broadcast domain into small broadcast domain. If we need to make communication between different VLANs then we need a router. Router have the feature to provide communication between different networks. VLAN provides the logical network within a single physical network.
VLAN basic concepts to Configure VLAN in Cisco Switch
Every switchport works on separate collision domain. We can say each device connected with a switchport remains in separate collision domain. By default all switchports of a switch works in a single broadcast domain. It can be define as all the devices working in a single LAN remains in a single broadcast domain. The big network of single broadcast domain can be divided into different small broadcast domains by creating the VLANs in the network. Every VLAN have its own broadcast domain.
Breaking the large broadcast domain into small broadcast domains provides an extra layer of security in the network. The devices of different broadcast domains can not communicate with each other. The swithports can be configured to restrict the unauthorised use by unwanted devices. Management of networking devices become easier by creating VLANs. Network administrator can monitor the small network more efficiently than a large network.
Methods of adding devices in VLAN
The devices can be added in a VLAN by two methods static and dynamic. Actually we configure the switchports for access by device with these methods. Generally static method assigned to the VLANs as it is easy and secure method. In static method we add the switchports manually to a VLAN. Suppose I assign the switchport number 4 to VLAN 10. This switchport remains assigned to VLAN unless we manually change it or assign to another VLAN. By default all switchports assigned to a single VLAN. We need to assign each port manually to the required VLAN.
The other method is dynamic assignment of swithports to VLAN according to the IP address of a device or MAC address of the device. Suppose a device connected to switchport 2 and it belongs to VLAN 20. If you change the switchport of this device from 2 to 10 then the switchport 10 automatically assigned to VLAN 20 and the device will work as it was. Dynamic method works in high end switches, in normal switch we can use static methods only.
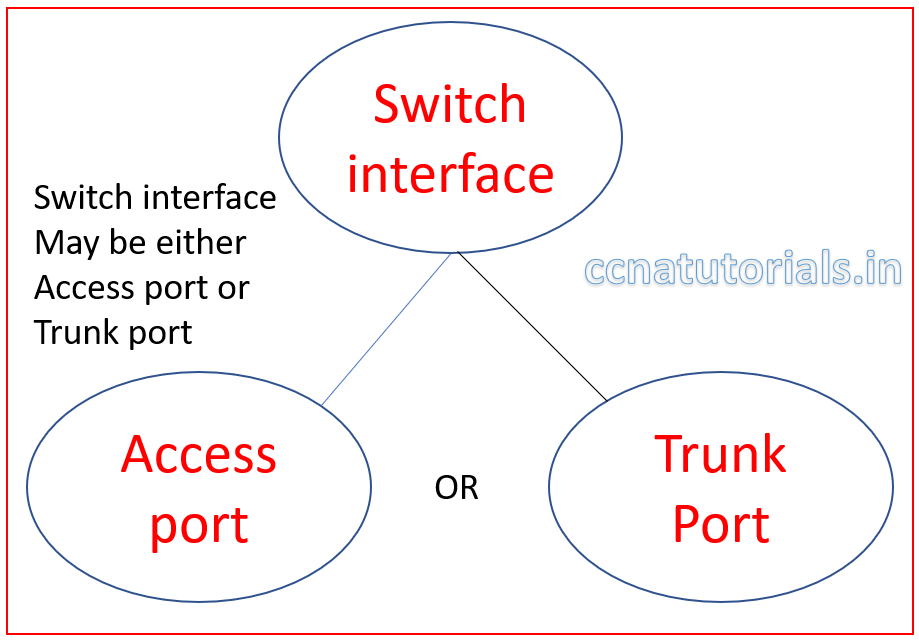
Access port and Trunk port for VLAN basic concepts
Access ports allow a device to access the network by using the NIC or RJ45 connection. The devices connected to access ports remains in same broadcast domain. The device can access, receive and transmit the data via access port. Generally all switchports remains as access ports until we manually convert them to trunk ports.
Trunk port mode allow to transmit and receive the data of multiple VLANs. Generally endpoint devices not connected with trunk ports. The networking devices uses trunk ports to connect with each other. For example when we need to connect two switches which have multiple VLANs, the switches can be connected via trunk ports. The assignment of access ports and trunk ports are logical. A switchport mode can be changed by using the command line interface.
Configure VLAN in Cisco switch
We can configure VLAN in Cisco Switch by some simple commands in CLI. A switch can hold VLAN from 1 to 4094. All interfaces of a switch remain in a single VLAN 1 by default. There are two tasks to configure VLAN in Cisco switch. Firstly, we assigned the VLAN in the switch. After assigning the VLAN number we bind the interfaces with VLAN. All devices connected with switch from one VLAN can communicate within VLAN. It is not possible for any device to communicate with other VLAN’s device. To enable the communication between different VLAN’s devices we need a router.
VLAN creates the broadcast domain in a switch. We know that by default the switch remains in single broadcast domain. Switchports breaks the collision domain. To break the broadcast domain, we require a router. router transfer the data packets from one network to another network. In VLAN the data packet doesn’t transfer to another network. The data packets remain in the same VLAN and flow between the devices. Before going to configure VLAN in Cisco switch, see the basic function of VLAN in cisco switch.
Function of VLAN in cisco switch.
The switch ports may be access port of trunk port. It is not possible that a port assigned both access and trunk properties. The function of access mode is simple. Access port received the data packets from the same VLAN from where the data packet transmitted. Access ports allow only single VLAN data transfer through it.
Trunk port can carry data packets of multiple VLAN at a time. VLAN makes the separate broadcast domain for each VLAN. The devices belong to a VLAN can communicate within the same broadcast domain or same VLAN. The network ID of different VLAN may be different or same. Network ID do not play any role in data transfer within a VLAN. Switchport interface assigned to particular VLAN. IP address of devices doesn’t matter for data transfer in VLAN.
Configure VLAN in Cisco Switch
We configure three VLAN in a cisco switch. Four interfaces assigned to each VLAN. I mean switchport 1-4 for VLAN 10, 5-8 for VLAN 20 and 9 -12 for VLAN 30. Port 24 mode set to trunk port. By default, all switchports remains in access mode. We do not need to change the mode of any switchport. Mode of switchport require to change when we need a trunk port. We can change the mode of any switchport from access to trunk and vice versa.
To configure VLAN in cisco switch firstly we define the VLANs after that we assigned the interfaces to each VLAN and try to ping the computer connected with different VLAN. I keep the same network ID for all devices of all VLANs. See whether the devices of different VLAN communicate with each other or not. We know the devices with same network ID in a network communicate with each other. See whether VLAN breaks the broadcast domain for different VLAN.
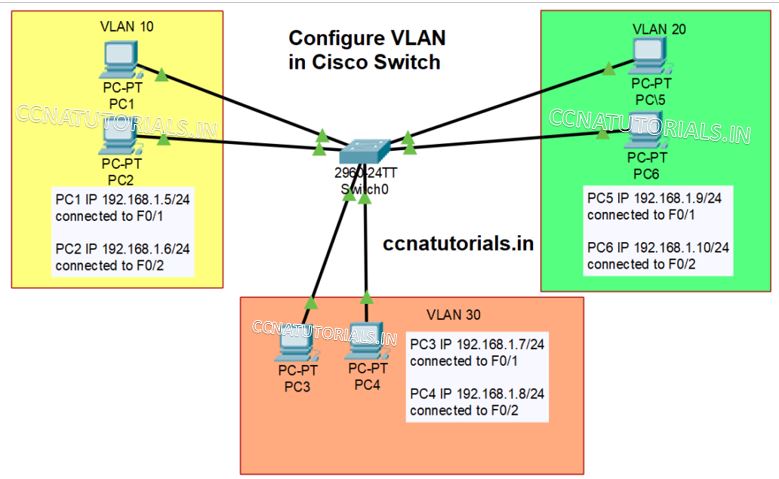
Design a small network like shown in picture shown above. Assign IP address of network ID 192.168.1.0/24 to all PC connected with the switch. Connect PC1 and 2 on switchport Fast Ethernet 0 and 1. Similarly connect PC3 and 4 with Fast Ethernet 5 and 6 and PC 5 and 6 with Fast Ethernet 9 and 10. We set the VLAN 10, 20 and 30 in switch. Now try to ping all PC with each other. You can all PC can ping each other. Now we configure the different PCs to different VLANs.
Commands to configure VLAN in cisco switch
Follow the commands shown in below command window to create VLAN 10, 20 and 30.
Switch>enable Switch# Switch#vlan database Switch(vlan)#vlan 10 VLAN 10 added: Name: VLAN0010 Switch(vlan)#vlan 20 VLAN 20 added: Name: VLAN0020 Switch(vlan)#vlan 30 VLAN 30 added: Name: VLAN0030 Switch(vlan)#exit APPLY completed. Exiting.... Switch#wr Building configuration... [OK] Switch#
Three new VLAN created by running above commands. You can check the created VLAN by running “show vlan” command in command line interface. See the example below.
Switch#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 VLAN0010 active
20 VLAN0020 active
30 VLAN0030 active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
1 enet 100001 1500 - - - - - 0 0
10 enet 100010 1500 - - - - - 0 0
20 enet 100020 1500 - - - - - 0 0
30 enet 100030 1500 - - - - - 0 0
1002 fddi 101002 1500 - - - - - 0 0
1003 tr 101003 1500 - - - - - 0 0
1004 fdnet 101004 1500 - - - ieee - 0 0
1005 trnet 101005 1500 - - - ibm - 0 0
VLAN Type SAID MTU Parent RingNo BridgeNo Stp BrdgMode Trans1 Trans2
---- ----- ---------- ----- ------ ------ -------- ---- -------- ------ ------
Remote SPAN VLANs
------------------------------------------------------------------------------
Primary Secondary Type Ports
------- --------- ----------------- ------------------------------------------
Switch#
Assigning ports to VLAN in a cisco switch
We have created three VLANs in Cisco switch. As shown in above command line all interfaces of switch belong to VLAN1. We must assign the switchports belongs to related VLAN. Assign switchport 1 to 4 to VLAN 10, 5 to 8 to VLAN20 and 9 to 12 to VLAN 30.
Assign FastEthernet ports to relate VLANs
We need to assign the switchports to related VLAN one by one. We need to run following commands in CLI to assign the switchports to VLAN. I am showing only two switchports for example. You must assign all switchports to different VLAN. To assign switchport F0/1 and F0/2 to VLAN 10 run the following commands.
Switch> Switch>enable Switch# Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet0/1 Switch(config-if)#switchport access vlan 10 Switch(config-if)#exit Switch(config)#interface fastethernet0/2 Switch(config-if)#switchport access vlan 10 Switch(config-if)#exit Switch(config)#exit Switch# %SYS-5-CONFIG_I: Configured from console by console Switch#wr Building configuration... [OK] Switch#
Similarly assign the remaining switchports to VLAN 20 and 30.
Switch> Switch>enable Switch# Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#interface FastEthernet0/5 Switch(config-if)#switchport access vlan 20 Switch(config-if)#exit Switch(config)#interface fastethernet0/6 Switch(config-if)#switchport access vlan 20 Switch(config-if)#exit Switch(config)#exit Switch(config)#interface FastEthernet0/9 Switch(config-if)#switchport access vlan 30 Switch(config-if)#exit Switch(config)#interface fastethernet0/10 Switch(config-if)#switchport access vlan 30 Switch(config-if)#exit Switch(config)#exit Switch# %SYS-5-CONFIG_I: Configured from console by console Switch#wr Building configuration... [OK] Switch#
Try to ping the PC of VLAN 10 with PC of VLAN 20. You can see they are not communicating with each other. Only within VLAN PC can communicate with each other.
we hope you understand the concept of VLAN and configuration of VLAN in Cisco switch. For any query or suggestion on this article you may contact us or drop a comment below. Your suggestions are always welcome by us.







I like what you guys are up too. Such clever work and reporting! Keep up the superb works guys I?¦ve incorporated you guys to my blogroll. I think it’ll improve the value of my web site 🙂