In this article I describe the PING Packet Internet Groper in computer network for CCNA exam. PING Packet Internet Groper works on ICMP protocol in the network between different networking devices. PING Packet Internet Groper used for troubleshooting of a network. The PING Packet Internet Groper is simple request and response command which provide the availability of a device in the network. Some time PING Packet Internet Groper is used to check the response time in the network.
PING Packet Internet Groper command available in all networking devices like computer, laptop, switch, router and modem etc. The PING Packet Internet Groper works on the IP address of an interface of the device. IP address identify the interface connected with the network. You can use PING command following by the IP address of the interface of a device or the hostname of the device.
PING Packet Internet Groper and ICMP Internet Control Message Protocol
You can understood the PING Packet Internet Groper well if you know about the ICMP protocol function in a network. You need to type the Ping command following by the IP address or hostname for example “ping 127.0.0.1” or “ping localhost”. The response of ping command tells about the connectivity and response time. The response time measured in milliseconds. The response time indicates the data transfer speed on the network.
You may also check the response time of a website on the internet. If you got the response time less than 50ms, it means the data transfer speed between these devices is very good. Accordingly you can imagine the data transfer speed from the response time of ping between different devices. Before going to explanation of PING Packet Internet Groper lets remind the ICMP protocol which will help to understand the PING Packet Internet Groper command.
ICMP Internet Control Message Protocol definition
ICMP Internet Control Message Protocol is related to PING Packet Internet Groper command in the computer network. ICMP Internet Control Message Protocol works on internet layer of TCP/IP Suite model. The ICMP Internet Control Message Protocol provides the troubleshooting and testing the connectivity between different devices on a network or internet. ICMP Internet Control Message Protocol provide the facility to check the data flow speed between different devices on network or internet. ICMP Internet Control Message Protocol mostly used to check the network congestion and route of data packet in all networks like TCP/IP network and Cisco Three layered hierarchical network.
ICMP Internet Control Message Protocol does not send any data in the network between devices. ICMP Internet Control Message Protocol used to check the connectivity and data flow speed in the network. All networking devices and endpoint devices of the network can use the ICMP Internet Control Message Protocol. ICMP packets are different from other data packets.
ICMP Internet Control Message Protocol in brief
ICMP Internet Control Message Protocol is an internet layer protocol in TCP/IP model. The ICMP protocol provides error reporting, troubleshooting of network devices in a network. ICMP works with IP protocol, as IP protocol is a connectionless and unreliable protocol. ICMP is mostly used by ping and traceroute command. Data lost reporting is main responsibility of ICMP protocol. Ping command show the data transmitted and received quantity. Counting of lost packets monitored and reported by the ICMP protocol to all device in a network.
ICMP is a part of IP protocol. IP protocol use ICMP protocol to send the error message to network devices. ICMP use IP protocol for transporting message. So, both IP and ICMP protocol are complements to each other in a network.
Some errors encountered by ICMP Internet Control Message Protocol
Time Exceeded error. As suggested by this message text, this error shows the time exceeded in data delivery. This message generated in two conditions. The first condition is when a router is running out of space and take so much time to deliver the data packets. Another reason of this message is any host is not receiving the datagrams to reassemble the packets. Host is reachable in this condition. Host unreachable is another error countered by ICMP Internet Control Message Protocol.
Route Redirect error. This error occurs when a host sent wrong addressee to a router. Generally, a host send datagram to a router who have the route of its destination. In case router doesn’t have the route for a datagram packet then Route Redirect error occurs.
Host Unreachable. When the destination not found for delivery of a datagram host unreachable message floated.
Echo request and Echo reply in PING Packet Internet Groper ICMP
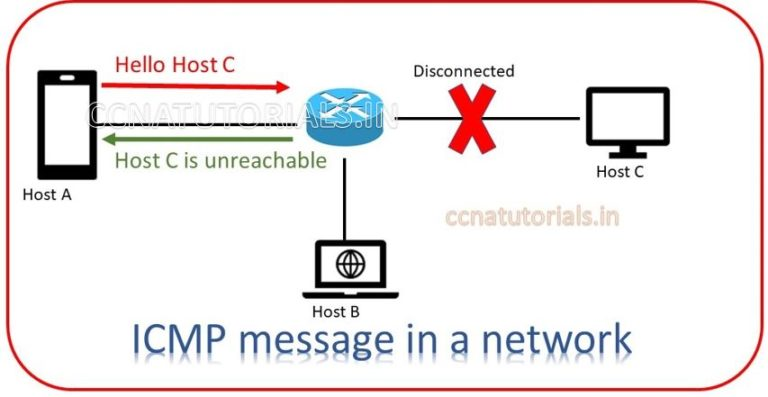
Echo request and Echo reply used to check the connectivity between two hosts in a network. PING Packet Internet Groper command is best example of Echo request and Echo reply message. PING Packet Internet Groper command is used to check the connectivity between two hosts. Host A wants to check the connectivity with host B. User will run PING Packet Internet Groper command in host A for host B. host A sent 4 packets in the network with addressee header of host B. host A send Echo request in the network. If Host B is connected in network and ICMP enable on its firewall, then Host B receive the Echo request and send Echo reply to host A. it is a complete cycle of echo request and echo reply in a network.
Function of PING Packet Internet Groper with ICMP Internet Control Message Protocol
General errors always generate in a network. ICMP Internet Control Message Protocol is responsible to monitor these errors and info to related networking device. network devices like routers generate error message and send to source IP address. All networking device are capable to send, receive and process the ICMP Internet Control Message Protocol. Suppose a gate way is out of reach to router. A host in the network send a packet to the destination which is away from the gateway. Router will generate an error message host is not reachable and send to the intended host. This process is done by a set of rules, which followed by ICMP Internet Control Message Protocol. For IPv4 addressing system ICMP4 functions for error reporting. For IPv6 ICMP6 functions for error reporting.

PING Packet Internet Groper explained in brief
PING Packet Internet Groper is a general command prompt based program to check the availability of an IP address and response. PING Packet Internet Groper is a diagnose command which send a ICMP request to the interface of any device in the network. The result of PING Packet Internet Groper command provide the information about the availability of requested IP address and the response time from it. Ping can be used with some predefined characters like -a and -t.
Ping is a very common networking utility program. PING Packet Internet Groper test the reachablity to a particular host or networking device in a network. It is not necessary if a device is physically connected, the device is reachable. There are many reasons due to a physically connected device not reachable. To trace out the problem PING Packet Internet Groper command firstly run. PING supports any physically linked device in network. The Ping command supports device as well as IP address.
PING Packet Internet Groper sends data packet to the device. The device send reply for PING data packet to the sender. The whole process result out whether the device are reachable or not. If sender did not get the reply within a due time it will show request time out. Ping provide the data speed and reliability of data in the network.
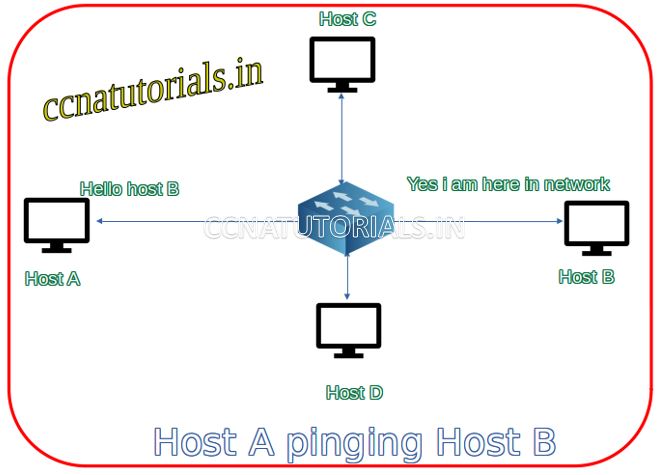
Working of PING command
The aim of PING command is to check the reachablity of a particular domain or device. PING send an ICMP echo request to particular IP address and test the connectivity by receiving reply. ICMP is Internet Control Message Protocol. Generally ICMP packets blocked by firewall for security purpose. A network administrator troubleshoot the network by PING utility. PING command works on all platforms like windows, linux and MAC. Packet Internet Groper works in command prompt in windows and in terminal in linux.
Execution of PING Packet InterNet Groper in a network
The Ping utility uses the echo request, and echo reply messages within the Internet Control Message Protocol (ICMP), an integral part of any IP network. When a ping command is issued, an echo request packet is sent to the address specified. When the remote host receives the echo request, it responds with an echo reply packet.
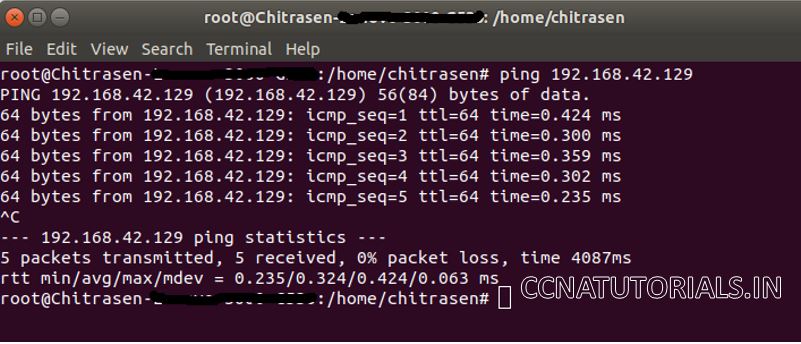
PING command sends ICMP echo requests. The outcome of echo request message shown in command prompt. The result show how many packets were send and hos many received. The result also show the TTL and time taking in response to a ICMP packet. User identifies the response of device and speed receiving and sending packets.
Format of PING Packet
A PING packet contains 4 bytes. Type of protocols IPv4 or Ipv6 similarly the ICMP version also included in packet. For IPv4 ICMP and for IPV6 ICMP6 protocol used by PING command. Below these information the identifier and sequence number included with payload. The reply of this ICMP packet must include the same payload. Time to receive the request is different thing it can be change for each packet and every time.
PING Packet Internet Groper statistics
What ICMP packet send and receive let’s take a look. After execution of PING command some data appears on command window.
ping ccnatutorials.in Pinging ccnatutorials.in [ 162.215.240.128 ] with 32 bytes of data: Reply from 162.215.240.128: bytes=32 time=4ms TTL=55 Reply from 162.215.240.128 : bytes=32 time=4ms TTL=55 Reply from 162.215.240.128 : bytes=32 time=4ms TTL=55 Reply from 162.215.240.128 : bytes=32 time=4ms TTL=55 Ping statistics for 162.215.240.128 : Packets: Sent = 4, Received = 4, Lost = 0 (0% loss), Approximate round trip times in milli-seconds: Minimum = 4ms, Maximum = 4ms, Average = 4ms
In above result bytes=32 show the size of packet. Time=4ms showing the time between sending and receiving ICMP packet. TTL =55 means the time to live for each packet.

Terms used in PING command result
Various switches used for PING command that are used for specific purpose. For example -t is used to send continue the ICMP packets. Without -t only four packets send to check the reachablity of a particular host. Below are some switches used with PING command.
Number :- sets the number of ICMP echo requests to be sent. By default number set to 4. by default 4 packets sent in one time command. User can change the numbers of ICMP packet required to sent.
Timeout :– The default value of timeout is 4 seconds in windows. User can change the timeout value as per requirement.
Size :– Here size denotes the ICMP packet size. By default the packet size remains 32 bits. User can changes the size of the ping packet.
TTL :- This switch can be used to change the Time to live of packet.
Error codes in PING Command
TTL Expired in Transit- TTL stands for Time To Live. This value indicates the living time of an ICMP packet in the network. Destination Host Unreachable– this message indicates that the host you want to communicate is not available in this network. Request Timed Out it means no any reply message received. Unknown Host this message indicates that the required host is not available in the network.
explaination of PING command with the operators available in linux terminal command prompt is shown below in the command window
PING(8) NAME ping - send ICMP ECHO_REQUEST to network hosts SYNOPSIS ping [-aAbBdDfhLnOqrRUvV46] [-c count] [-F flowlabel] [-i interval] [-I interface] [-l preload] [-m mark] [-M pmtudisc_option] [-N nodeinfo_option] [-w deadline] [-W timeout] [-p pattern] [-Q tos] [-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp option] [hop ...] destination DESCRIPTION ping uses the ICMP protocol's mandatory ECHO_REQUEST datagram to elicit an ICMP ECHO_RESPONSE from a host or gateway. ECHO_REQUEST datagrams (``pings'') have an IP and ICMP header, followed by a struct timeval and then an arbitrary number of ``pad'' bytes used to fill out the packet. ping works with both IPv4 and IPv6. Using only one of them explicitly can be enforced by specifying -4 or -6. ping can also send IPv6 Node Information Queries (RFC4620). Intermediate hops may not be allowed, because IPv6 source routing was deprecated (RFC5095). OPTIONS -4 Use IPv4 only. -6 Use IPv6 only. -a Audible ping. -A Adaptive ping. Interpacket interval adapts to round-trip time, so that effectively not more than one (or more, if preload is set) unanswered probe is present in the network. Minimal interval is 200msec for not super-user. On networks with low rtt this mode is essentially equivalent to flood mode. -b Allow pinging a broadcast address. -B Do not allow ping to change source address of probes. The address is bound to one selected when ping starts. -c count Stop after sending count ECHO_REQUEST packets. With deadline option, ping waits for count ECHO_REPLY packets, until the timeout expires. -d Set the SO_DEBUG option on the socket being used. Essentially, this socket option is not used by Linux kernel. -D Print timestamp (unix time + microseconds as in gettimeofday) before each line. -f Flood ping. For every ECHO_REQUEST sent a period ``.'' is printed, while for ever ECHO_REPLY received a backspace is printed. This provides a rapid display of how many packets are being dropped. If interval is not given, it sets interval to zero and outputs packets as fast as they come back or one hundred times per second, whichever is more. Only the super-user may use this option with zero interval. -F flow label IPv6 only. Allocate and set 20 bit flow label (in hex) on echo request packets. If value is zero, kernel allocates ran‐ dom flow label. -h Show help. -i interval Wait interval seconds between sending each packet. The default is to wait for one second between each packet normally, or not to wait in flood mode. Only super-user may set interval to values less than 0.2 seconds. -I interface interface is either an address, or an interface name. If interface is an address, it sets source address to specified interface address. If interface in an interface name, it sets source interface to specified interface. For IPv6, when doing ping to a link-local scope address, link specification (by the '%'-notation in destination, or by this option) is required. -l preload If preload is specified, ping sends that many packets not waiting for reply. Only the super-user may select preload more than 3. -L Suppress loopback of multicast packets. This flag only applies if the ping destination is a multicast address. -m mark use mark to tag the packets going out. This is useful for variety of reasons within the kernel such as using policy routing to select specific outbound processing. -M pmtudisc_opt Select Path MTU Discovery strategy. pmtudisc_option may be either do (prohibit fragmentation, even local one) -O Report outstanding ICMP ECHO reply before sending next packet. This is useful together with the timestamp -D to log out‐put to a diagnostic file and search for missing answers. -p pattern You may specify up to 16 ``pad'' bytes to fill out the packet you send. This is useful for diagnosing data-dependent problems in a network. For example, -p ff will cause the sent packet to be filled with all ones. -q Quiet output. Nothing is displayed except the summary lines at startup time and when finished. -Q tos Set Quality of Service -related bits in ICMP datagrams. tos can be decimal (ping only) or hex number. In RFC2474, these fields are interpreted as 8-bit Differentiated Services (DS), consisting of: bits 0-1 (2 lowest bits) of separate data, and bits 2-7 (highest 6 bits) of Differentiated Services Codepoint (DSCP). In RFC2481 and RFC3168, bits 0-1 are used for ECN. Historically (RFC1349, obsoleted by RFC2474), these were interpreted as: bit 0 (lowest bit) for reserved (currently being redefined as congestion control), 1-4 for Type of Service and bits 5-7 (highest bits) for Precedence. -r Bypass the normal routing tables and send directly to a host on an attached interface. If the host is not on a directly- attached network, an error is returned. This option can be used to ping a local host through an interface that has no route through it provided the option -I is also used. -R ping only. Record route. Includes the RECORD_ROUTE option in the ECHO_REQUEST packet and displays the route buffer on returned packets. Note that the IP header is only large enough for nine such routes. Many hosts ignore or discard this option. -s packetsize Specifies the number of data bytes to be sent. The default is 56, which translates into 64 ICMP data bytes when combined with the 8 bytes of ICMP header data. -S sndbuf Set socket sndbuf. If not specified, it is selected to buffer not more than one packet. -t ttl ping only. Set the IP Time to Live. -T timestamp option Set special IP timestamp options. timestamp option may be either tsonly (only timestamps), tsandaddr (timestamps and addresses) or tsprespec host1 [host2 [host3 [host4]]] (timestamp prespecified hops). -U Print full user-to-user latency (the old behaviour). Normally ping prints network round trip time, which can be different f.e. due to DNS failures. -v Verbose output. -V Show version and exit. -w deadline Specify a timeout, in seconds, before ping exits regardless of how many packets have been sent or received. In this case ping does not stop after count packet are sent, it waits either for deadline expire or until count probes are answered or for some error notification from network. -W timeout Time to wait for a response, in seconds. The option affects only timeout in absence of any responses, otherwise ping waits for two RTTs. When using ping for fault isolation, it should first be run on the local host, to verify that the local network interface is up and running. Then, hosts and gateways further and further away should be ``pinged''. Round-trip times and packet loss statistics are computed. If duplicate packets are received, they are not included in the packet loss calculation, although the round trip time of these packets is used in calculating the minimum/average/maximum round-trip time numbers. When the specified number of packets have been sent (and received) or if the program is terminated with a SIGINT, a brief summary is displayed. Shorter current statistics can be obtained without termination of process with signal SIGQUIT. If ping does not receive any reply packets at all it will exit with code 1. If a packet count and deadline are both specified,and fewer than count packets are received by the time the deadline has arrived, it will also exit with code 1. On other error it exits with code 2. Otherwise it exits with code 0. This makes it possible to use the exit code to see if a host is alive or not. This program is intended for use in network testing, measurement and management. Because of the load it can impose on the network, it is unwise to use ping during normal operations or from automated scripts. ICMP PACKET DETAILS An IP header without options is 20 bytes. An ICMP ECHO_REQUEST packet contains an additional 8 bytes worth of ICMP header followed by an arbitrary amount of data. When a packetsize is given, this indicated the size of this extra piece of data (the default is 56). Thus the amount of data received inside of an IP packet of type ICMP ECHO_REPLY will always be 8 bytes more than the requested data space (the ICMP header). If the data space is at least of size of struct timeval ping uses the beginning bytes of this space to include a timestamp which it uses in the computation of round trip times. If the data space is shorter, no round trip times are given. If the data space is at least of size of struct timeval ping uses the beginning bytes of this space to include a timestamp which it uses in the computation of round trip times. If the data space is shorter, no round trip times are given. DUPLICATE AND DAMAGED PACKETS ping will report duplicate and damaged packets. Duplicate packets should never occur, and seem to be caused by inappropriate link-level retransmissions. Duplicates may occur in many situations and are rarely (if ever) a good sign, although the presence of low levels of duplicates may not always be cause for alarm. Damaged packets are obviously serious cause for alarm and often indicate broken hardware somewhere in the ping packet's path (in the network or in the hosts). TRYING DIFFERENT DATA PATTERNS The (inter)network layer should never treat packets differently depending on the data contained in the data portion. Unfortunately, data-dependent problems have been known to sneak into networks and remain undetected for long periods of time. In many cases the particular pattern that will have problems is something that doesn't have sufficient ``transitions'', such as all ones or all zeros, or a pattern right at the edge, such as almost all zeros. It isn't necessarily enough to specify a data pattern of all zeros (for example) on the command line because the pattern that is of interest is at the data link level, and the relationship between what you type and what the controllers transmit can be complicated. This means that if you have a data-dependent problem you will probably have to do a lot of testing to find it. If you are lucky, you may manage to find a file that either can't be sent across your network or that takes much longer to transfer than other sim‐ ilar length files. You can then examine this file for repeated patterns that you can test using the -p option of ping. TTL DETAILS The TTL value of an IP packet represents the maximum number of IP routers that the packet can go through before being thrown way. In current practice you can expect each router in the Internet to decrement the TTL field by exactly one. The TCP/IP specification states that the TTL field for TCP packets should be set to 60, but many systems use smaller values (4.3 BSD uses 30, 4.2 used 15). The maximum possible value of this field is 255, and most Unix systems set the TTL field of ICMP ECHO_REQUEST packets to 255. This is why you will find you can ``ping'' some hosts, but not reach them with telnet(1) or ftp(1). In normal operation ping prints the TTL value from the packet it receives. When a remote system receives a ping packet, it can do one of three things with the TTL field in its response: · Not change it; this is what Berkeley Unix systems did before the 4.3BSD Tahoe release. In this case the TTL value in the received packet will be 255 minus the number of routers in the round-trip path. · Not change it; this is what Berkeley Unix systems did before the 4.3BSD Tahoe release. In this case the TTL value in the received packet will be 255 minus the number of routers in the round-trip path. · Set it to 255; this is what current Berkeley Unix systems do. In this case the TTL value in the received packet will be 255 minus the number of routers in the path from the remote system to the pinging host. · Set it to some other value. Some machines use the same value for ICMP packets that they use for TCP packets, for example either 30 or 60. Others may use completely wild values. BUGS · Many Hosts and Gateways ignore the RECORD_ROUTE option. · The maximum IP header length is too small for options like RECORD_ROUTE to be completely useful. There's not much that can be done about this, however. · Flood pinging is not recommended in general, and flood pinging the broadcast address should only be done under very controlled conditions. HISTORY The ping command appeared in 4.3BSD. The version described here is its descendant specific to Linux. As of version s20150815, the ping6 binary doesn't exist anymore. It has been merged into ping. Creating a symlink named ping6 pointing to ping will result in the same funcionality as before. SECURITY ping requires CAP_NET_RAW capability to be executed 1) if the program is used for non-echo queries (See -N option), or 2) if ker‐ nel does not support non-raw ICMP sockets, or 3) if the user is not allowed to create an ICMP echo socket. The program may be used as set-uid root.
In this article I described the PING Packet Internet Groper in computer networking. I hope you found this article helpful for CCNA exam. For any query or suggestions you may contact us or drop a comment below. your suggestions are always welcome by us.






It’s a shame you don’t have a donate button! I’d certainly donate to this fantastic blog!
I suppose for now i’ll settle for book-marking and adding your
RSS feed to my Google account. I look forward
to brand new updates and will talk about this site with my Facebook
group. Talk soon!
The Obesity Code Netflix Best Books Vacation 2019
my page :: pdf book (ioplux.shoppy.pl)