Contents of this article
In this article, I describe IPv6 Duplicate Address Detection (DAD): Ensuring Address Uniqueness and Network Stability. In the ever-expanding landscape of networking, IPv6 Duplicate Address Detection (DAD) stands as a foundational mechanism that ensures the uniqueness and integrity of IPv6 addresses within a network. As the successor to the Duplicate Address Detection process in IPv4, DAD plays a pivotal role in preventing address conflicts, enhancing network stability, and promoting efficient communication. In this comprehensive exploration, we delve into the intricacies of IPv6 Duplicate Address Detection, shedding light on its purpose, mechanics, significance, and real-world applications. Let’s see the IPv6 Duplicate Address Detection (DAD).
Understanding IPv6 Duplicate Address Detection (DAD):
IPv6 Duplicate Address Detection (DAD) is a process through which devices joining an IPv6 network verify that the IPv6 address they intend to use is unique within that network. Address conflicts can lead to communication disruptions and hinder the functionality of networked devices. DAD ensures that devices can confidently configure and use IPv6 addresses without the risk of clashes.
The Purpose of DAD:
The primary purpose of DAD is to prevent address conflicts by detecting whether another device in the same network is already using the same IPv6 address. DAD guarantees that each device’s IPv6 address is unique, which is vital for seamless communication and efficient routing within the network.
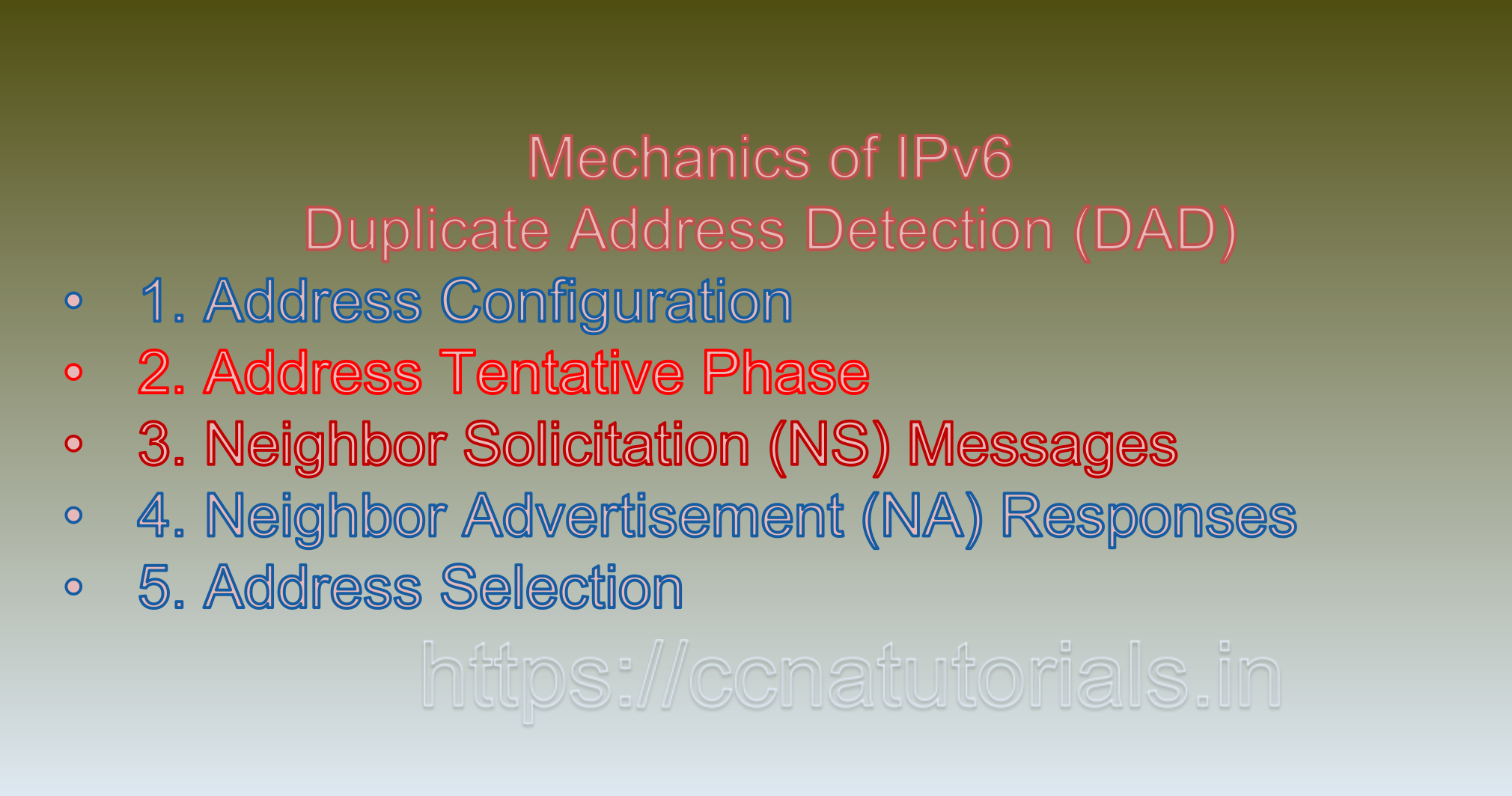
Mechanics of IPv6 Duplicate Address Detection (DAD):
DAD operates when a device configures a new IPv6 address, typically during the process of address autoconfiguration, which can be either stateless or stateful. The process involves the following steps:
1. Address Configuration:
When a device joins an IPv6 network, it uses information from Router Advertisement (RA) messages to configure its IPv6 address.
2. Address Tentative Phase:
Before a device begins using its newly configured IPv6 address for communication, it enters a tentative phase. During this phase, the device considers the address “tentative” and does not use it for any outgoing communication.
3. Neighbor Solicitation (NS) Messages:
The device sends a Neighbor Solicitation (NS) message to inquire whether the configured address is already in use by another device in the network.
4. Neighbor Advertisement (NA) Responses:
If no device responds to the NS message, it indicates that the address is unique, and the device proceeds to the next steps. However, if another device responds with a Neighbor Advertisement (NA) message, indicating that the address is already in use, the device concludes that a conflict exists.
5. Address Selection:
In case of a conflict, the device performs address selection algorithms to choose an alternate IPv6 address.
6. Tentative Address Use:
If the address is deemed unique, the device transitions from the tentative phase to the “preferred” state, allowing it to use the address for communication.
Real-World Applications and Significance:
The importance of IPv6 Duplicate Address Detection extends to various aspects of networking and communication:
1. Preventing Address Conflicts:
DAD prevents situations where multiple devices claim the same IPv6 address, ensuring that data packets reach the intended recipients without conflicts.
2. Network Stability:
By detecting and resolving address conflicts, DAD contributes to network stability and minimizes disruptions that may arise from duplicate addresses.
3. Autoconfiguration Confidence:
DAD enhances the reliability of address autoconfiguration, enabling devices to confidently configure and use IPv6 addresses without worrying about potential clashes.
4. Efficient Routing:
Unique addresses enable routers to accurately route data packets to their destinations, optimizing network performance.
5. Address Lifetime Management:
DAD ensures that devices do not use duplicate addresses, simplifying address lifetime management and preventing confusion.
Example Scenario for IPv6 Duplicate Address Detection (DAD):
Imagine a scenario where a new laptop joins a corporate IPv6 network. As the laptop connects to the network, it automatically configures an IPv6 address using Router Advertisement messages. However, before it starts using the configured address for communication, the laptop performs DAD. It sends a Neighbor Solicitation message to check if any other device is using the same address. If no response is received, the laptop concludes that the address is unique and proceeds to use it. On the other hand, if a response is received, indicating a conflict, the laptop selects an alternate address to ensure seamless communication.
Security and Considerations:
While IPv6 Duplicate Address Detection enhances network reliability, it’s important to note that the process may introduce a brief delay before a device starts using its address for communication. Additionally, DAD itself is vulnerable to attacks like Address Flooding and Denial of Service (DoS) attacks. Implementing security measures, such as rate-limiting Neighbor Solicitation messages, can help mitigate these risks.
Ensuring Order and Reliability with DAD:
IPv6 Duplicate Address Detection (DAD) serves as a crucial pillar of network stability and efficiency. By ensuring the uniqueness of IPv6 addresses and preventing conflicts, DAD empowers devices to communicate seamlessly within IPv6 networks. As networks continue to expand and evolve, the role of DAD remains essential in promoting reliable communication, efficient routing, and a cohesive digital ecosystem where devices confidently exchange data without the disruption of address clashes.
IPv6 Duplicate Address Detection (DAD): Ensuring Address Uniqueness and Network Harmony
IPv6 Duplicate Address Detection (DAD) is a fundamental process that safeguards the uniqueness and stability of IPv6 addresses within a network. It plays a critical role in preventing address conflicts and promoting seamless communication among devices. Let’s delve into the concept of IPv6 DAD with illustrative examples to grasp its significance, mechanics, and real-world applications.
Understanding IPv6 Duplicate Address Detection (DAD):
IPv6 DAD is a mechanism that ensures the uniqueness of IPv6 addresses within a network. When a device configures a new IPv6 address, DAD verifies whether that address is already in use by another device. This prevents address conflicts and supports efficient data transmission.
Example 1: Unique Address Assignment:
Consider a scenario in a home network where a new smartphone joins. The smartphone uses Stateless Address Autoconfiguration (SLAAC) to configure an IPv6 address. Before using this address, DAD ensures its uniqueness.
1. The smartphone configures the address `2001:db8:1234:abcd::1234`.
2. It enters the tentative state, considering the address as “tentative” and refraining from using it for communication.
3. The smartphone sends a Neighbor Solicitation (NS) message to the all-nodes multicast address, asking if anyone else is using `2001:db8:1234:abcd::1234`.
4. If there’s no response, DAD concludes that the address is unique, and the smartphone proceeds to use it for communication.
5. However, if another device responds with a Neighbor Advertisement (NA) message, indicating that it is using the same address, DAD triggers a conflict resolution process.
Example 2: Conflict Resolution:
Suppose another device in the same network, like a tablet, is already using the address `2001:db8:1234:abcd::1234`. When the smartphone sends an NS message, the tablet responds with an NA message, indicating a conflict.
1. The smartphone receives the NA message from the tablet, indicating that the address is already in use.
2. DAD determines that a conflict exists, and the smartphone enters an address selection process to choose an alternate unique address.
3. The smartphone configures a new address, such as `2001:db8:1234:abcd::5678`, and repeats the DAD process.
Practical Applications:
IPv6 DAD has practical implications that enhance network operation:
1. Address Uniqueness:
DAD prevents devices from using duplicate addresses, ensuring efficient communication and data integrity.
2. Autoconfiguration Reliability:
DAD enhances the reliability of address autoconfiguration mechanisms, such as SLAAC, by confirming address uniqueness before usage.
3. Stable Communication:
By preventing address conflicts, DAD contributes to stable and disruption-free communication within the network.
Example 3: Network Expansion:
Imagine a corporate network where a new employee’s laptop connects for the first time. The laptop, using SLAAC, configures the address `2001:db8:abcd::1234`.
1. The laptop enters the tentative state and sends an NS message to verify address uniqueness.
2. If no response is received, DAD confirms the address’s uniqueness, and the laptop uses it for communication.
3. However, if an NA message is received, indicating a conflict, the laptop selects an alternate address, such as `2001:db8:abcd::5678`.
Security Considerations:
While DAD enhances network reliability, it can be vulnerable to attacks like Address Flooding. Malicious actors might flood the network with fake NA messages to disrupt DAD. Implementing measures like rate-limiting NS messages can help mitigate such risks.
Conclusion of IPv6 Duplicate Address Detection (DAD):
IPv6 Duplicate Address Detection (DAD) functions as the conductor that ensures every device in the network sings a unique and harmonious tune. By preventing address conflicts, DAD contributes to seamless communication, stable network operations, and efficient data transmission. As networks evolve and expand, the role of DAD remains essential in creating an environment where devices confidently and reliably communicate, ensuring that each IPv6 address is a distinctive note in the symphony of modern networking.






