Contents of this article
In this article I describe TACACS in network security. It is necessary to know about some network security basic concepts along with management of networking devices. We know there are a lots of threats available on internet. Similarly for any network there are many ways to effect the network from virus and hackers. If your network is connected with internet, it is not safe.
There are many types of vulnerability in a network connected with internet. Hackers from all over the world always try to get information from any network. You can safe your network from these attacks by understanding some network security basic concepts. Now a lots of devices transfers data over the internet over wired, wireless and cellular networks.
Network security protects the devices from unauthorized access and malfunction activities. Malfunction activities can modify or destroy the data. The major cause of data theft is frequently use of internet from mobile and computers. We share personal data on social sites and do financial transaction on internet. The data shared on internet is always on risk from hackers and attackers. To keep safe the data from unauthorized access network security is necessary. We can prevent the attacks on our devices by aware about network security basic concepts.
Network security is necessary to protect the own networking devices and clients from unauthorized access, destruction and malfunction etc. Internet is the main resource of security threats. We manage the network for protection from these threats. We can say network security is all about to protect our internet connected computers from virus and hackers. You can manage our network security by using some firewalls, router etc. We allow unauthorized access to unknown persons by compromising own network security.
TACACS in network security
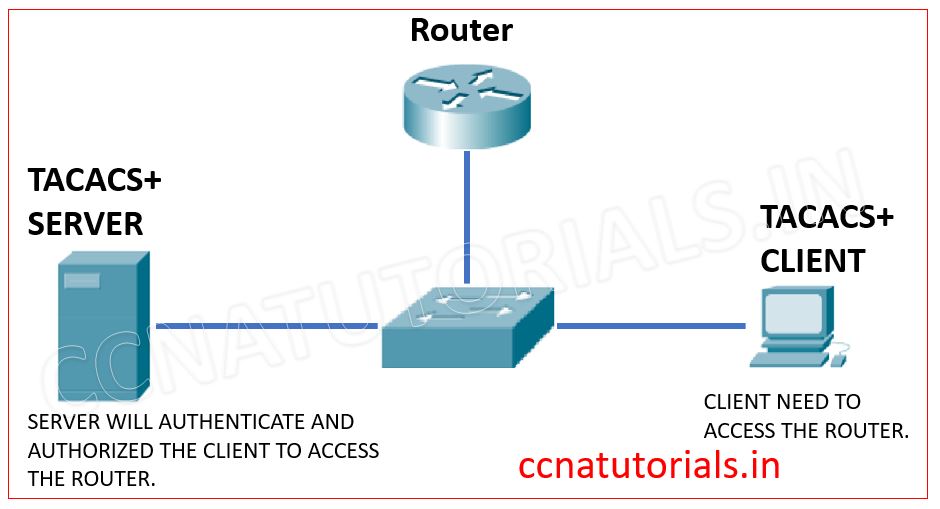
TACACS is acronym for Terminal Access Controller Access Control Server. TACACS is a network protocol provide secure remote connection of network devices which is used in AAA framework. TACACS is very similar to RADIUS. The purpose of RADIUS in network security is to authenticate and authorize user access to a remote network. TACACS works on client server architecture which allow remote access or network devices with a central server.
TACACS works on TCP network protocol. TACACS uses TCP port 49. TACACS provide security for unauthorized access with a combination of authentication and authorization with a single process. Firstly the authentication is required the user authorized for network services. In server client architecture for TACACS the clients are networking devices like switch and routers.
Benefits of TACACS in network security
TACACS is a propriety of CISCO which works in AAA framework. AAA is known as Authentication, Authorization and accounting service. TACACS uses TCP protocol and port number 49. TACACS service transfer all packets in encrypted format during communication between client and ACS server. All AAA services separated with each other means Authentication Authorisation and accounting are separated from each other’s.
Function of TACACS in network security
A TACACS server provide the access of network devices to the clients. When a client need to access any network device, client prompt for username firstly. After submission of username a prompt for password appears in client’s screen. After successfully submission of username and password the TACACS responds with ACCEPT, REJECT and ERROR message. ACCEPT message means the credentials entered are valid and client got the access of required network device. Similarly REJECT means the credentials are not valid. If there is any problem in the link between TACACS and client then ERROR message occurs.
Configuration of TACACS in network security
The configuration of TACACS in network security is very similar to the configuration of RADIUS. First thing we need to configure TACACS service in router is to enable the AAA service. AAA service is known as Authentication Authorization and Accounting. Run aaa new-model command in global configuration mode see below command window.
Router>enable Router#config t Router(config)#aaa ? accounting Accounting configurations parameters. authentication Authentication configurations parameters. authorization Authorization configurations parameters. new-model Enable NEW access control commands and functions.(Disables OLD commands.) Router(config)#aaa new-model Router(config)#do wr Building configuration... [OK]
This command allow local authentication to all interfaces and lines of router. Now configure a local username and password by running the below commands. Local user authentication is required to access the router in case of failure from external authentication. For example I set username is admin and password is root.
Router(config)#username admin password root Router(config)#do wr Building configuration... [OK]
Now configure the TACACS server and key by running the below commands. Here server name is tacacslogin and key is secureloginkey.
Router(config)#radius server securelogintacacs+ Router(config-radius-server)#address ipv4 10.10.10.1 Router(config-radius-server)#key TACACS+PASSWORD Router(config-radius-server)#exit Router(config)#do wr Building configuration... [OK]
Configuration of RADIUS server completed by running above commands. Now we need to add this newly created TACACS server to AAA group of any name. Run the below commands to allow TACACS group.
Router(config)#aaa authentication login default group MyTACACS+Group local
After running above all commands you successfully configured the TACACS in router.
I hope you found this article helpful related to configuration of TACACS in network security. For any query or suggestion you may contact us or drop a comment in the below comment form. Share this article if you found this helpful.




Thanks for helping out, fantastic info .